Teams apps are becoming more and more popular as the usage for Teams is increasing. The app store provides access to numerous apps created by Microsoft as well as other vendors. There are few different approaches that you can take to allow or restrict app access. Whether you decide to completely restrict access or allow access based on usage, it is important to understand the impact of teams app access polices and its implication related to security. The tips and recommendations in this article prioritizes security and compliance, while giving users access to apps that they need. These recommendations are best suited for financial and healthcare industries which has stricter compliance requirements.
Org-wide app settings
As the name implies, the org-wide app settings determines the global settings for the apps that controls third-party apps and custom apps. You can access org-wide app settings by selecting “Teams app -> manage apps” from the left pane of the Teams admin Center. The button for the setting will appear on the top right corner.
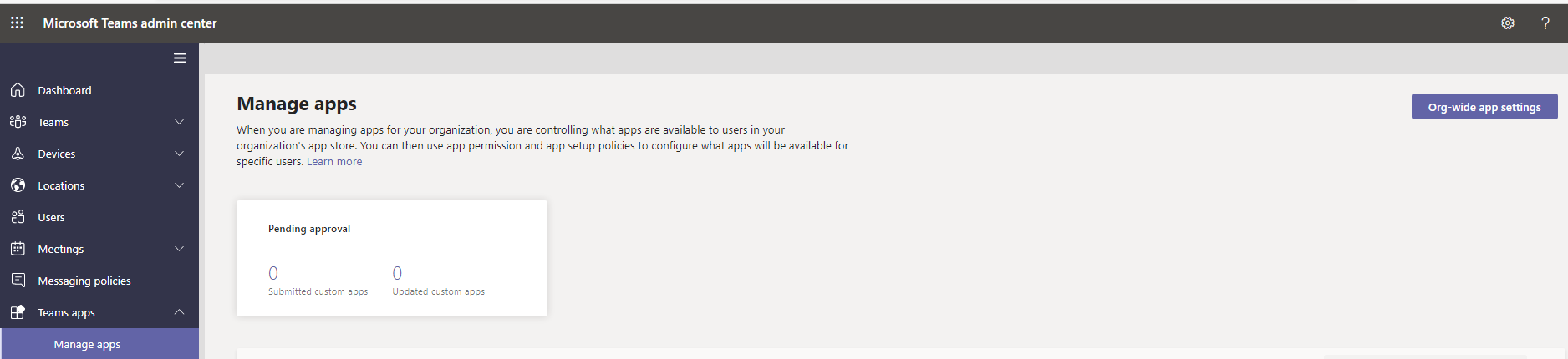
Third-party apps
In general, most organizations have these turned off. It is very hard to control which apps are being downloaded by user and what type of data is being accessed. Unless you have a small set of savvy users, the broad access to all 3rd party apps should be turned off.
The second option allows any new 3rd party apps to be used by the users assuming the first options is turned on. New apps are always a higher risks in terms of security and compliance. Therefore, this should be turned off even if you allow users access to all or certain 3rd party apps.
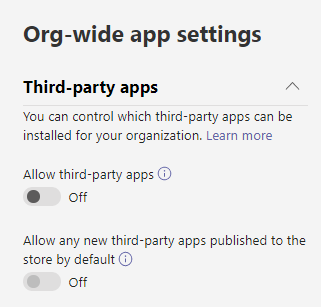
Custom Apps
Unless you are using custom app, this should be turned off. If you turn this ‘ON’ you should restrict the access via permission policy, otherwise, all user will also have the ability to upload custom apps. If you are using custom app, then, turn this setting ON, and make sure change the global policy so that users can only access custom policy but cannot upload it. You will need to create a separate policy for the developers of custom app.
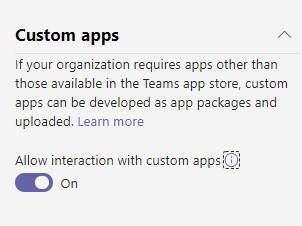
App Permission Policy
The app permission policy determines which apps user have access to. The policies are applied to users directly. Therefore, you can create multiple policies for different set of users. Or, you can modify the global policy to your need. Also, note that, you can create a special policy for your developers to test, upload and publish apps.
Microsoft Apps
Note that these also contain apps that are published by Microsoft partners. All of these apps go through basic testing and guideline for a secure app however, your organization may have specific data and information security needs. More importantly, the underlying idea behind security is to give access to only what is needed, not more. Therefore, the recommendation is to “Allow specific apps and block all others”. Note that, if you choose to block all apps, then, certain features of Teams will not work. Most organizations allow all Microsoft apps and it is not a major issue. The reason for allowing all apps is that, Teams is designed to be used as a collaboration platform for entire office suite. Therefore if someone in your organization is using a something like “Power BI” then, they should be able to add the app in Teams and then collab or share “Power BI” report.
Depending on your licenses your users may have access to a large number of Microsoft apps and may choose to collab on teams platform using these apps. However, adding apps does not add license. For example: UserA has Office 365 E5 license but does not have Microsoft Project license, but the user adds Project from Teams app, the user in this case, will not be able to use project.
If you do not want to allow “all Microsoft apps” to all users, then, the other option is to have two different polices – One policy for regular users who only use a small set of Microsoft apps such as – word, excel, powerpoint. The other policy is for “Super Users” who will potentially use large number of Microsoft apps. It is possible to customize the app permission policy so that every group of users only have access to apps that they use, the downside is that, it may become a tedious administrative task since more and more apps are becoming available and proving to be highly productive.
Following is the screenshot of a policy with two specific Microsoft Apps. Note that, you have to know the name of the app in the search window for adding the app. It does not show all the apps.
Thrid-Party Apps
If you want to allow few 3rd party apps, the best approach is to select the option to allow only specific apps – then, allow only those apps that have been vetted by the security and app developer teams in your organization. In this case, you will unblock third-party apps from the org-wide settings.
Custom Apps
Last option is for custom apps, in this, case also you can either allow all custom apps or specific apps. Usually, it is best practice, to allow only those custom apps that have been tested and approved by the organization. Often times, developers may publish beta version of apps for testing, if you allow all custom apps then, it will become available for all users. Therefore, all custom apps should only be available to developers.
If your organization has large number of apps, or apps that access restricted data set then, you might want to setup policy that provided access to specific custom apps to specific groups of users.
App Setup Policy
Setup policy determines if the app will be installed automatically and which apps will be pinned on the teams client interface. Setup policy has a dependency on the permission policy. Only apps that are permitted can be installed on Teams – whether it is automatic install by policy or manually installed by user.
Pro Tip
You want to create custom app permission policy and app setup policy in pairs. Even though you can have two app setup policies and one app permission policy, it is best to have a 1:1 relation.
The first option “upload custom apps” is the ability to upload custom apps, only developers who create and test custom apps for Teams should have a policy with this option turned on. The Global policy along with all other user policies should have this option turned off.
Installed Apps:
The apps listed in the installed Apps will install the apps for the user whether they select it or not. The apps that are allowed in “Permission Policy” will be available for the user to install, but it will not install itself automatically. Note that when you search for the “installed apps” the search option lets you select a specific permission policy and then search result is narrowed down to that policy. This way, you can avoid any conflict. Otherwise, it is possible that the app that you selected to be installed is not permitted by the permission policy.
Pinned Apps:
This controls the way apps are pinned in the navigation bar. You can also choose the priority to move the apps up and down. You can pin many apps for the users. If they all do not fit in the left menu bar of the Teams desktop app then, the “more added apps” (…) option will show rest of the pinned teams.

Summary:
Technet has very detailed information along with powershell commands for all settings that were discussed. It may get confusing as to where to start, which one to do first. Following are the steps in chronological order that I usually follow.
- Understand you overall recommendation first and briefly note down the polices and settings required to achieve your goal. You should note down :
- How many sets of users are there based on apps access and usage
- What changes are needed in the org-wide settings and global polices
- How many app permission policies are needed
- How many app setup polices are needed
- Make changes to the org-wide settings.
- Modify Global Policy based on requirements – this will be the policy that gets applied to the majority of the users.
- Modify the global app setup policy – this should complement the global permission policy.
- Create a custom policy for specific group of users who have requirements that is different than the global policy.
- Create custom setup policy that complements the permission policy in step 5.
- Apply correct set of app permission policy and setup policy to the appropriate group of users.
- If you are planning to develop custom apps make sure to create app permission and app setup policy specific for developers.



